Since Russia’s invasion of Ukraine on February 24, 2022, denial-of-service (DoS) attacks impacting availability have been rising. The attacks aren’t only affecting Russia and Ukraine either. Public and private organizations in multiple industries have been impacted, and several nations—including the U.S. and U.K.—have issued warnings about cyberthreats from Russia.
A recent report from the Uptime Institute notes some 60% of outages cost at least $100,000, and 15% cost at least $1 million. Falling victim to one of these attacks can significantly impact your bottom line.
In this post, we’ll take a closer look at recent attacks attributed to Russia, how different DoS attacks work, and what you can do to help keep your site available.
What Attacks Have Been Seen in the Wild?
Let’s start by looking at some of the significant availability threats and attacks that have occurred in recent months.
BrownFlood Malicious JavaScript Code
According to CERT-UA#4553, attackers have been embedding malicious JavaScript code in compromised websites (mostly sites running WordPress) to perform distributed DoS (DDoS) attacks against various Ukrainian Government and pro-Ukraine sites. When a visitor accesses a compromised site, this executes the malicious BrownFlood code, and the visitor’s computer subsequently spams the target sites with requests.
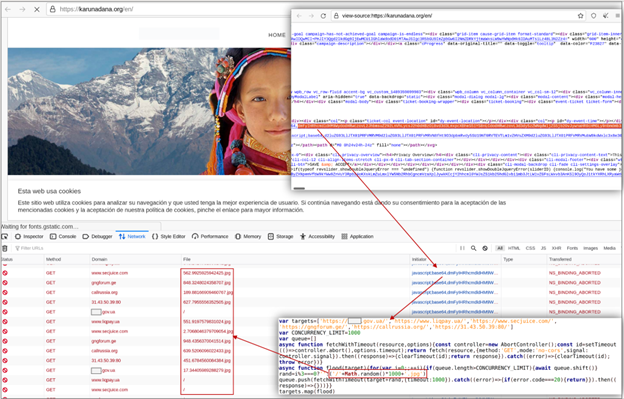
Source: https://cert.gov.ua/article/39923
Researchers have discovered versions of BrownFlood using Math.random() to generate URIs in their requests, but attackers may modify this approach in the future. Malicious BrownFlood code can be embedded in HTML, JavaScript, and other website assets and is often obfuscated with base64 encoding.
DDoS Attacks Against Ukrainian Banks
The U.K. Foreign, Commonwealth & Development Office and National Cyber Security Centre indicated Russia was likely responsible for DDoS attacks against several Ukrainian banks before the invasion. The attacks occurred February 15 – 16, 2022, and the report suggests the Russian Main Intelligence Directorate (GRU) was involved.
While the details of the DDoS attacks are unclear, The Register confirmed the websites of PrivatBank and Oschadbank were knocked offline at the time. PrivatBank ATMs and online transactions were also affected.
Attacks Against Russia
Separate from attacks by Russia, there are many “hacktivists” launching attacks against Russia. An NBC News report indicated that DDoS attacks are the most visible way pro-Ukraine hackers are attempting to make an impact. One of the things making DDoS attacks so appealing to hacktivists is they’re relatively technically simple to execute and lead to immediate results.
Politically or Militarily Motivated Attacks
Unfortunately, the Russia-Ukraine War isn’t the first instance of politically or militarily motivated DDoS attacks. As evidence of the evolving digital world, recent history has brought several other examples, including:
- DDoS attack against Israeli communications providers: In March 2022, a DDoS attack—labeled the largest ever against Israel—against Israeli communications providers took down multiple government websites and led to a state of emergency.
- DDoS attack against NotePad++ because of their Free Uyghur edition: The popular NotePad++ text editor fell victim to a DDoS attack after releasing its 7.8.1 version, titled the “Free Uyghur edition.”
- DDoS attack against PopVote: In 2014, before the Hong Kong protests known as the “Umbrella Movement,” the PopVote public opinion voting system was hit by the largest DDoS attack in history at the time.
What’s the takeaway here? While it’s true organizations dealing with finance, government, and critical infrastructure directly related to the Russia-Ukraine War have an increased risk, they’re far from the only ones needing to be concerned.
In fact, The Hacker News reports education, tech, healthcare, and online gaming are all common targets. Additionally, you don’t have to be a large enterprise to be a target. Small and medium-sized enterprises are common targets of threat actors looking to compromise availability.
How Do the Attacks Work?
Now we know the what, let’s look into how different attacks against availability work. All these attacks against availability fall into the category of DoS attacks. However, a “DoS attack” can take several different forms. Threat actors use various techniques to implement DoS attacks.
Let’s cover the three main categories of DoS attacks and how they work.
Volume-Based DoS Attacks
Volume-based DoS attacks are classic DoS. They generate more load (requests) than a server can handle, and as the server tries to keep up with the malicious requests, its bandwidth is exhausted. As a result, legitimate users are unable to access the server.
Common examples of volume-based DoS attacks include:
- UDP floods: This type of attack exploits how responses to UDP packets work. If there’s no service listening on a port, then the server sends an Internet Control Message Protocol (ICMP) error response. In a UDP flood, these error responses consume the server’s bandwidth and lead to denial of service.
- ICMP (ping) floods: An ICMP echo request (a ping) elicits an echo reply. With an ICMP flood, attackers exploit this behavior by spamming a site with pings to overload it.
- NTP amplification: Network Time Protocol (NTP) amplification attacks involve spoofing a victim’s IP address in NTP request packets. The attacker sends the NTP requests to NTP servers, but the servers reply to the victim’s address.
Protocol Attacks
Protocol attacks exploit vulnerabilities in the network and transport layers of the OSI model. Instead of compromising availability by exhausting bandwidth, protocol attacks exhaust processing capacity.
Synchronize (SYN) flood attacks are a great example of a protocol attack. In a SYN flood attack, the attacker sends many TCP SYN packets—these packets are the first step in the TCP handshake—with spoofed IP addresses. The server responds to the spoofed addresses with a SYN-ACK. Because the IP addresses were spoofed, the server never receives the acknowledge (ACK) response to the SYN-ACK. Eventually, if the server is left waiting for too many responses, it may crash or hang.
Layer 7 Attacks
Layer 7 (also known as the application layer) attacks exploit application layer protocols like HTTP to force a server to exhaust its resources. Application layer attacks are particularly tricky to deal with for two reasons:
- It’s hard to distinguish legitimate layer 7 traffic from malicious layer 7 traffic.
- A relatively small request can trigger a large amount of server resource consumption.
For example, an attacker may send HTTP GET or POST requests to the same API endpoints as legitimate users would. The attacker, however, sends requests at a much higher frequency or with specifically crafted headers and payloads.
How Can You Protect Your Sites?
Fortunately, there are several ways you can protect sites against availability threats from Russia and beyond. The following tools and techniques can help make your websites more resilient:
- Using a load balancer to distribute traffic across multiple servers
- Using a web application firewall (WAF) to provide traffic filtering and monitoring
- Applying Geo-IP filtering to block traffic from specific origins
- Turning off unused or unneeded services, which could otherwise be exploited (for example, ping responses)
- Using a content delivery network (CDN) to serve static content
- Implementing CAPTCHA-style challenges to prevent automated attacks
Additionally, it’s essential to remember the need for real-time monitoring. Proactive monitoring allows you to quickly detect and respond to anomalies, which can make a world of difference when mitigating the impact of an attack. Specifically, sites should implement the following:
- Resource monitoring: Real-time monitoring of server resources like CPU and network I/O can help detect anomalies, possibly indicating a DoS attack is in progress. For example, a spike in CPU utilization might be related to a SYN flood. The sooner you detect it, the sooner you can mitigate it.
- Uptime and performance monitoring: In addition to detecting outages, website monitoring with tools like Pingdom® enables you to detect “brownouts” (degraded performance) before they become “blackouts” (complete outages).
Detect Availability Issues Globally and Locally With Pingdom
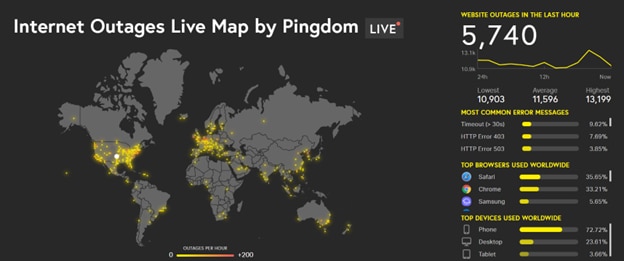
DoS threats from Russia significantly affect website availability and performance across the internet. The landscape is constantly changing, with attacks and countermeasures forming a constant cat-and-mouse game. With the Pingdom State of the Internet live map, you can stay up to date with a real-time view of website outages around the world.
If you’re interested in going beyond a global view and monitoring your own site’s availability, sign up for a 30-day free trial of Pingdom today!